Browsing on the internet can be troublesome at times. First, there might be GEO restrictions, making the webpage you are interested in unavailable. Second, some data might be too sensitive, and you feel insecure about entrusting it to vanilla HTTPS-protocol, let alone HTTP. Thirdly, you might want to establish a corporate network, separated from the rest of the web.
Luckily, all these tasks are achievable to a different degree, depending on the tools used. When it comes to anonymity and confidentiality online, there are at least three alternatives: Proxy, VPN, and Tor. More often than not, these terms are used interchangeably, yet each of them works differently, and we are about to learn how to protect your data online.
Proxy-Server
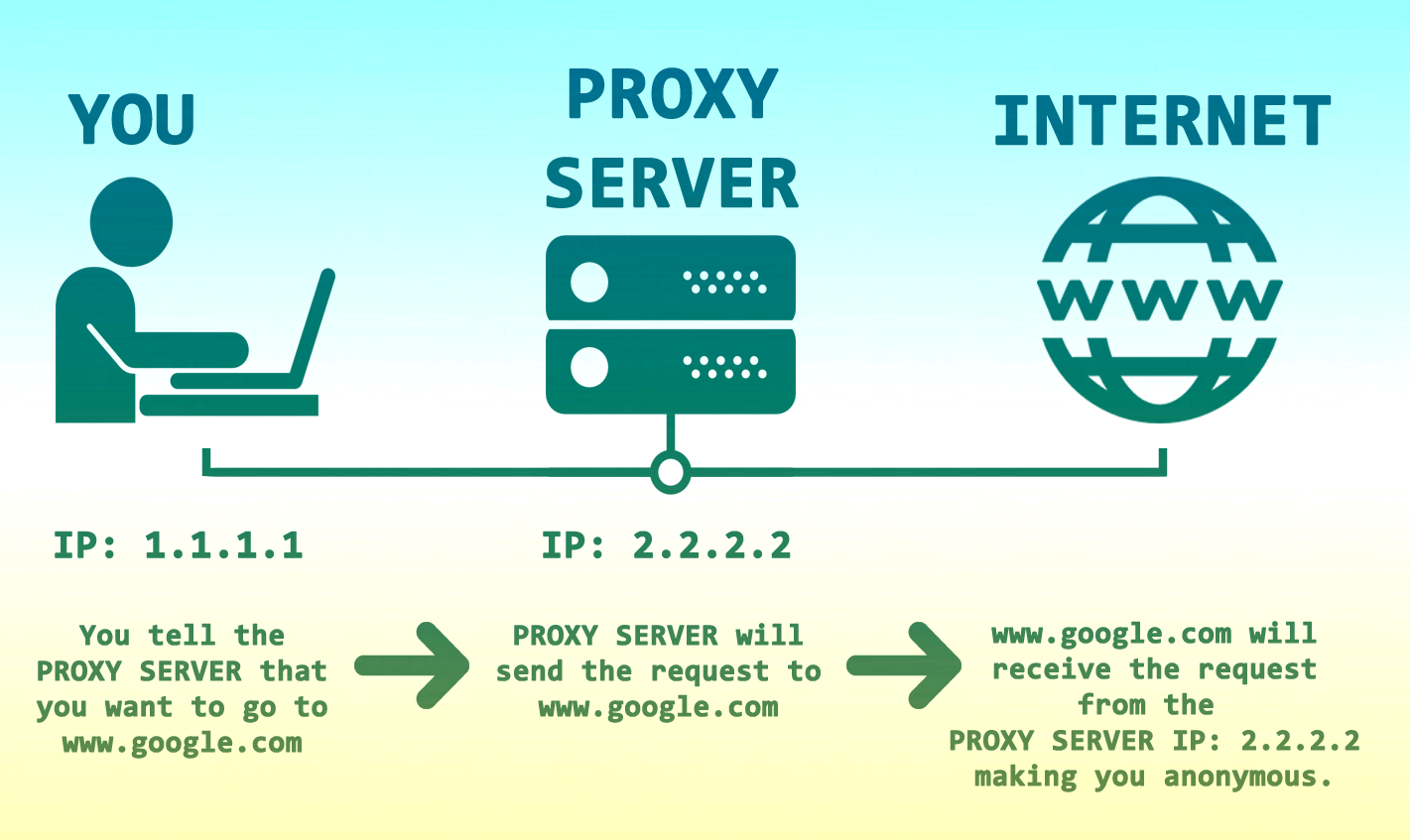
Proxy-server is the simplest technology of the trine above. As the name suggests, proxy-server, or simply proxy, is the middleman between a user and server. There are two main types of proxy-servers: forward proxy and reverse proxy. The main difference is that the former is used by the user, while the server uses the latter. Hereinafter, by saying proxy, we will refer to the forward type.
Using proxy is like hiring a porter to carry your luggage for you. It is usually done to maintain your privacy and identity online by separating yourself from the traffic you run. Confidentiality is not the only benefit of using proxy:
- Circumventing GEO restrictions (Chinese websites)
- Accessing locale-limited website versions (American NetFlix)
- Discovering location-specific discounts and special offers
- Caching the data for quicker future browsing
- Lowering traffic loading by compressing all the content
- Establishing web content policy (Schools, Corporate servers)
- Saving a lot on costs
Although the advantages are many, there are many substantial disadvantages to using proxy. For instance, the majority of proxies are highly specialized, meaning each website protocol will need a separate proxy: FTP-connection needs FTP-proxy, HTTPS-protocol requires HTTPS-proxy etc. Of course, there is the SOCKS-proxy, capable of working with different protocols, but this versatility comes at a price – significantly reduced browsing speed.
Speed is the lesser evil, because proxies can be insecure at times. Proxies do provide anonymity by changing your IP, but they grant no additional encryption whatsoever. It means HTTP-connection will be utterly at hackers’ mercy and HTTPS-traffic will be protected by SSL-encryption only.
Returning to our example with the porter above, you are entrusting a suitcase with your data and no lock to another person to deliver it safely. Can you really trust the porter you have picked up? Free proxies with bad reputation can get you into trouble like getting your data sold or simply being registered at every step.
Virtual Private Network
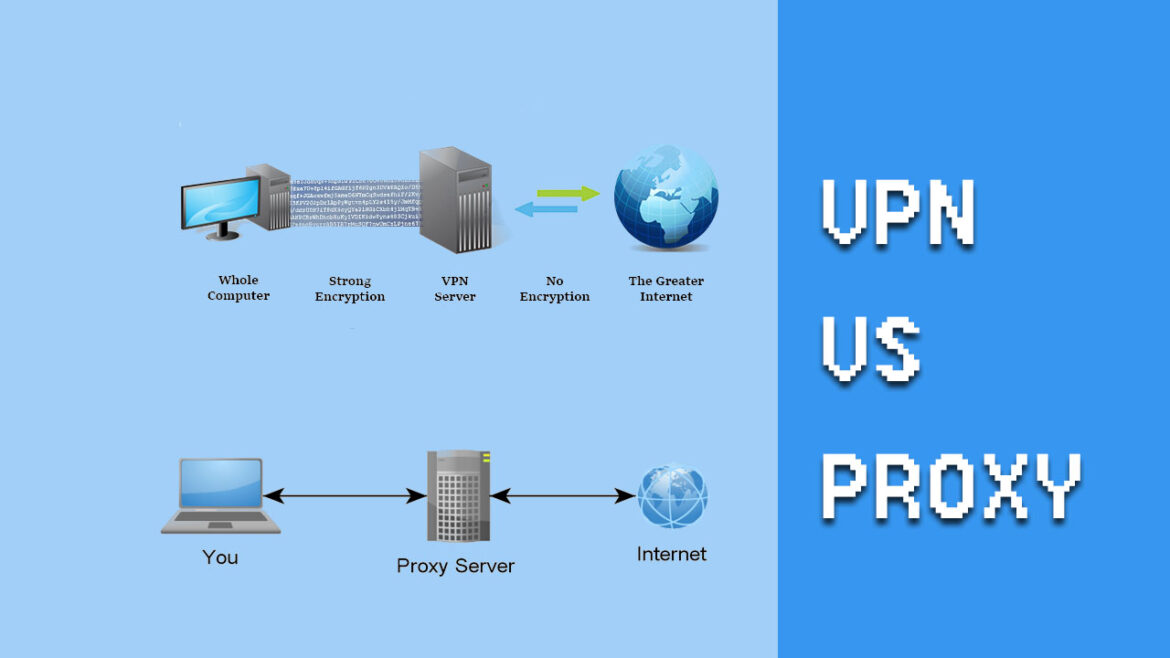
VPN is a technology, free from the majority of Proxy drawbacks, while retaining most of its bright sides. VPN is also a middleman between a user and the server, but unlike proxy, all the incoming and outgoing traffic is encrypted with the end-to-end encryption.
Initially, VPN was created not for anonymity, but rather for connecting computers into a single domain. VPN also maintains your privacy online, by replacing your IP; it also allows visiting GEO restricted websites.
Compared to the example with the porter, VPN transfers all kinds of traffic via special tunnel that can barely be accessed by any intruder. The traffic is not limited to the browser one, but includes other apps as well. VPN is best used for handling sensitive data, connecting to a public Wi-Fi, or for remote working.
Unlike proxy, you are going to need a dedicated client for VPN, either via an app or browser extension. Still, downloading one can be simpler than adjusting proxy settings in the browser.
VPN is not always a superior option, despite the advantages being obvious. VPN, especially the free versions, are also prone to data gathering and selling to a third party, e.g., Betternet, Hola.
Some proxies, like Shadowsocks, allow you to mask your traffic only partially. This allows you to have convenient access to different GEO without having to switch your IP. On the other hand, no proxy is made for anonymity. In fact, this peculiarity allows Shadowsocks to bypass different restrictions simultaneously, thanks to casual HTTPS-traffic that raises no suspicion. Therefore, VPN smokes the competition in terms of anonymity, but proxy might be better for breaching GEO limitations. Just make sure to use the programs you can trust.
The Onion Router
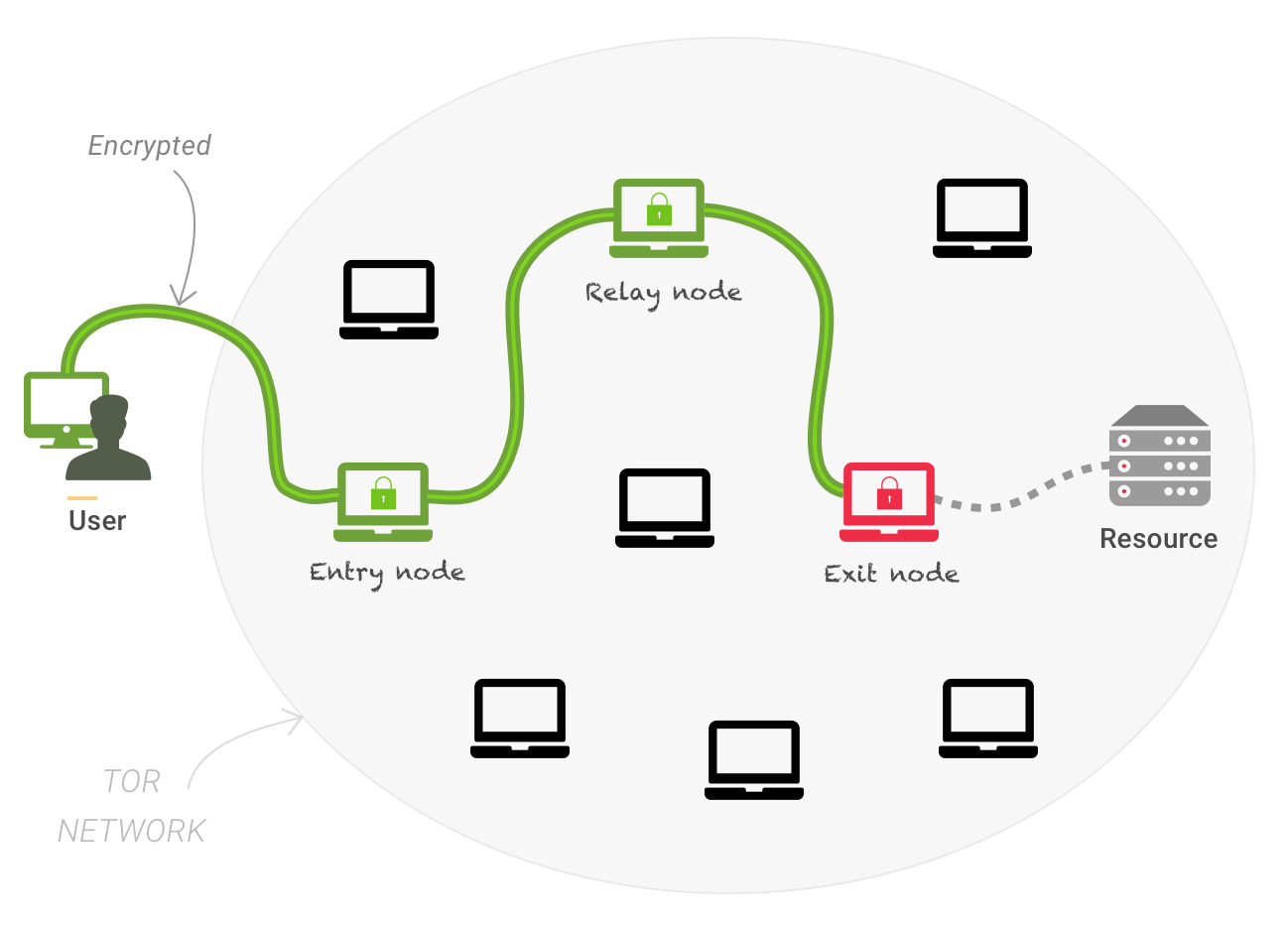
The Onion Router technology uses several nodes, which act as the middleman. Instead of having just one, TOR is based around 3 proxy servers. Each subsequent node knows only the IP address of the previous one, making it improbable to discover the initial IP address. Only the final node is aware of the traffic you run. The entry and middle nodes have to unwrap the defense layers before proceeding further.
While TOR enforces encryption and forbids all kinds of data gathering, the fact of using it is very noticeable. Therefore, TOR can cause an unwanted attention, meaning you may consider using TOR in tandem with VPN.
Next, the node owners are at risk, because they are responsible for all the data passing through. Finally, the owners of the exit node see all the running traffic. Indirectly, they can track it back to the very source.
Furthermore, multiple-layer encryption causes TOR to run slow. Many websites do not work as intended under the TOR browser. And if you follow the advice above about combining TOR with VPN, the connection speed will drop below the reasonable level.
Conclusion
Choosing between Proxy and VPN will depend on your budget and goals. Traffic encryption can either be done by VPN or TOR. But just to bypass or enforce content restrictions, the proxy option will be more than enough.
TOR is a great VPN-alternative, but the fact of using it is very noticeable in the first place. Multi-layer encryption is extremely safe, but damages your connection speed significantly. Whatever software you choose, make sure the source is trustworthy, because under the facade of anonymity can be spying tools, designed specifically to gather data on you in order to sell it afterward to the higher bidder.
If you want to reach new GEOs and audiences, maybe it is all waiting for you on Telegram? We’ve prepared some material about Telegram audiences. What are the messenger’s users like this year? How old they are, what they do, and what they are interested in!